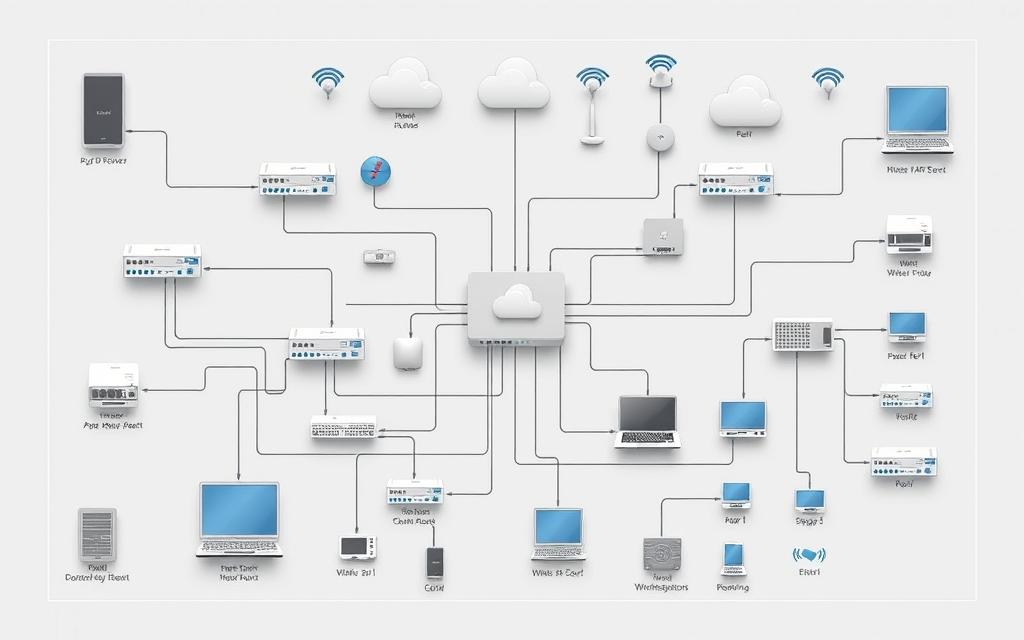
Modern organizations rely heavily on interconnected systems to share resources and communicate efficiently. These systems, known as computer networks, enable seamless collaboration across devices and locations. With over 90% of companies using LAN or WAN, their importance cannot be overstated.
Networks break geographical barriers, allowing teams to work together globally. They consist of nodes, such as computers and servers, connected through communication protocols. These protocols ensure smooth data exchange, making operations faster and more reliable.
Scalability is another critical feature of networks. As businesses grow, their network infrastructure must adapt to handle increased demands. This flexibility supports digital transformation, helping companies stay competitive in a rapidly evolving tech landscape.
Introduction to Computer Networks
From ARPANET to cloud-based infrastructures, networks have reshaped modern communication. Early systems like ARPANET laid the groundwork for today’s interconnected world, enabling seamless data exchange across devices and locations.
Modern networks boost operational efficiency by sharing resources like printers and databases. This collaborative approach reduces costs and enhances productivity, making it a cornerstone of business operations.
Packet-switching, a fundamental concept, ensures reliable data transfer. Protocols like TCP/IP break information into packets, route them efficiently, and reassemble them at the destination. This process minimizes errors and maximizes speed.
The Domain Name System (DNS) plays a critical role in translating domain names into IP addresses. Without DNS, accessing websites would require memorizing complex numerical sequences, hindering user experience.
Today, 85% of enterprises rely on hybrid network architectures. These systems combine on-premises and cloud-based solutions, offering flexibility and scalability to meet growing demands.
What Are the Components of a Computer Network?
Building a reliable system requires a blend of tangible and intangible elements working together. These elements form the backbone of seamless communication and resource sharing.
Physical devices like routers, switches, and NICs (Network Interface Cards) ensure data flows smoothly. Logical software components, such as network operating systems and protocols, manage and secure this flow.
In client-server architectures, centralized servers handle requests from multiple clients. Peer-to-peer setups, on the other hand, allow direct communication between nodes, offering flexibility and decentralization.
Emerging technologies like SDN (Software-Defined Networking) are reshaping traditional setups. SDN separates control and data planes, enabling dynamic management and scalability.
For enterprise-grade systems, redundancy is critical. Duplicate hardware and failover mechanisms ensure uninterrupted operations, even during failures.
- Physical components: Routers, switches, NICs, and cables.
- Logical components: Network operating systems, protocols, and services.
- Architectures: Client-server vs. peer-to-peer.
- Innovations: SDN for dynamic management.
- Redundancy: Essential for enterprise reliability.
Hardware Components of a Computer Network
The foundation of any reliable network lies in its physical devices. These hardware elements ensure seamless data transfer and connectivity. From Network Interface Cards to advanced routers, each component plays a critical role in maintaining system efficiency.
Network Interface Cards (NICs)
NICs connect devices to a network, enabling data exchange. PCIe NICs offer higher throughput, reaching up to 10Gbps, while USB NICs are more portable but cap at 1Gbps. Choosing the right NIC depends on speed and compatibility needs.
Switches
Modern switches operate at Layer 2, using MAC address filtering for efficient data routing. They support VLAN configurations and Power over Ethernet (PoE) capabilities, adhering to 802.3af/at standards. These features make switches ideal for scalable setups.
Routers
Routers manage data flow between networks, often implementing NAT for security. Enterprise-grade models support protocols like BGP and OSPF, ensuring optimal routing table management. Their ability to handle complex traffic makes them indispensable.
Hubs
Unlike switches, hubs create collision domains, leading to potential data conflicts. While they are simpler and cheaper, their inefficiency makes them less suitable for modern, high-demand environments.
Cables and Connectors
The choice of cables significantly impacts network performance. Cat6A cables support speeds up to 10Gbps, while OM4 fiber can handle 100Gbps. Selecting the right cabling ensures optimal data transfer rates and reliability.
| Cable Type | Speed | Use Case |
|---|---|---|
| Cat6A | 10Gbps | Office Networks |
| OM4 Fiber | 100Gbps | Data Centers |
Software Components of a Computer Network
The backbone of modern connectivity is powered by sophisticated software systems. These solutions ensure seamless communication, efficient resource sharing, and robust security across interconnected devices.
From operating systems to protocols, software plays a critical role in managing and optimizing network performance. Let’s explore the key elements that make this possible.
Network Operating System (NOS)
A Network Operating System (NOS) serves as the foundation for managing network resources. Proprietary solutions like Cisco IOS use CLI interfaces for precise control, while open-source options like VyOS offer flexibility and cost-effectiveness.
Modern NOS platforms incorporate API-driven automation, enabling dynamic management and scalability. This shift simplifies complex tasks and reduces manual intervention.
Network Protocols
Protocols define the rules for data exchange, ensuring reliability and security. TLS 1.3, for instance, enhances encryption during the handshake process, minimizing vulnerabilities.
QUIC, a newer protocol, reduces latency by combining transport and security layers. These advancements are reshaping how data travels across networks.
Network Services
Essential services like DHCP manage IP address allocation, ensuring devices can connect seamlessly. RADIUS provides secure authentication, verifying user credentials before granting access.
These services work behind the scenes to maintain network integrity and efficiency.
Emerging technologies like Software-Defined Networking (SDN) and Network Function Virtualization (NFV) are revolutionizing traditional setups. SDN controllers like OpenDaylight and ONOS enable centralized management, while NFV replaces hardware with virtualized functions.
Together, these innovations enhance flexibility, scalability, and cost-efficiency in modern networks.
Types of Computer Networks
Different systems connect devices in unique ways, each serving specific needs. These setups vary in scale, purpose, and capacity, enabling efficient communication across diverse environments. Understanding the distinct types helps organizations choose the right solution for their operations.
Local Area Network (LAN)
LANs connect devices within a limited area, such as an office or building. They offer high-speed data transfer, with Wi-Fi 6 deployments reaching theoretical speeds of 9.6Gbps. This setup is ideal for environments requiring fast and reliable connectivity.
Latency in LANs is typically under 1ms, ensuring real-time communication. These systems are cost-effective and easy to manage, making them a popular choice for businesses.
Wide Area Network (WAN)
WANs span larger geographical areas, connecting multiple LANs. They often use MPLS technology, ensuring 99.999% uptime. SD-WAN adoption is growing rapidly, with a projected 30% CAGR through 2026.
Latency in WANs ranges from 50-100ms, which is higher than LANs but suitable for long-distance communication. These systems are essential for organizations with multiple locations.
Metropolitan Area Network (MAN)
MANs cover a city or campus, offering a balance between LAN and WAN. They often use DWDM implementations in metro Ethernet, supporting up to 96 channels. This setup is ideal for institutions requiring high capacity over a medium range.
MANs provide faster speeds than WANs while covering a larger area than LANs. They are commonly used by universities and large enterprises.
Personal Area Network (PAN)
PANs connect devices within a personal space, typically using Bluetooth 5.3 or NFC. Bluetooth 5.3 offers speeds up to 40Mbps, enabling seamless data transfer between smartphones and wearables.
UWB (Ultra-Wideband) is another technology used in PANs, providing precise location tracking. These systems are perfect for individual use, enhancing personal device connectivity.
Network Topologies
Network topologies define the layout and flow of data between connected systems. These arrangements determine how devices communicate, ensuring efficient resource sharing and reliable performance. Choosing the right type of topology is crucial for optimizing network operations.
Bus Topology
In a bus topology, all nodes are connected to a single central cable. This setup uses CSMA/CD (Carrier Sense Multiple Access with Collision Detection) to manage data collisions. While simple and cost-effective, it struggles with scalability and performance in modern environments.
Star Topology
Star topologies feature a central hub connecting all devices. This design offers centralized management, making it ideal for modern data centers. If one connection fails, the rest of the network remains unaffected, ensuring high reliability.
Ring Topology
In a ring topology, devices are connected in a circular loop. Data travels in one direction, using token-passing mechanisms like those in FDDI implementations. This setup ensures equal access to resources but can be disrupted by a single failure.
Mesh Topology
Mesh topologies provide multiple paths for data transfer, enhancing reliability. Full-mesh setups offer n(n-1)/2 connections, ensuring redundancy. However, they face scalability challenges due to the high number of links required.
Hybrid Topology
Hybrid topologies combine elements of different layouts, such as spine-leaf designs in cloud data centers. This approach balances flexibility, scalability, and performance, making it suitable for complex systems.
| Topology | Advantages | Disadvantages |
|---|---|---|
| Bus | Simple, cost-effective | Limited scalability |
| Star | Centralized management | Dependent on central hub |
| Ring | Equal resource access | Single point of failure |
| Mesh | High reliability | Complex to manage |
| Hybrid | Flexible, scalable | Higher implementation cost |
Network Protocols
Effective communication across devices relies on standardized rules known as protocols. These rules ensure seamless data exchange, enabling applications to function smoothly. From browsing the web to sending emails, protocols are the backbone of modern connectivity.
Transmission Control Protocol/Internet Protocol (TCP/IP)
TCP/IP is the foundation of internet communication. It uses a three-way handshake to establish connections, ensuring reliable data transfer. Window scaling optimizes performance by adjusting the amount of data sent at once, reducing latency.
Hypertext Transfer Protocol (HTTP)
HTTP facilitates web browsing by defining how messages are formatted and transmitted. HTTP/3, powered by the QUIC protocol, uses UDP for faster transfer speeds. Native encryption enhances security, making it ideal for modern applications.
File Transfer Protocol (FTP)
FTP enables file sharing between devices. SFTP, a secure version, uses SSH for encryption, while FTPS relies on SSL/TLS certificates. Both ensure safe data exchange, but SFTP is simpler to manage.
Simple Mail Transfer Protocol (SMTP)
SMTP handles email delivery across networks. Frameworks like SPF, DKIM, and DMARC authenticate messages, preventing spam and phishing. These protocols ensure emails reach the correct address securely.
Domain Name System (DNS)
DNS translates domain names into IP addresses, making web navigation user-friendly. It uses UDP port 53 for queries and TCP port 53 for zone transfers. Anycast routing and TTL configurations enhance reliability and speed.
Network Security
Protecting sensitive data and ensuring uninterrupted operations are critical in today’s digital landscape. With cyber threats evolving rapidly, organizations must adopt robust measures to safeguard their systems. From malware attacks to unauthorized access, the risks are diverse and ever-present.
Effective security strategies combine advanced technologies and proactive practices. These measures not only defend against threats but also ensure compliance with industry standards. Let’s explore the key aspects of network protection.
Viruses and Malware
Malware remains a significant threat, with attackers using fileless techniques and living-off-the-land strategies. These methods bypass traditional defenses, making detection challenging. Regular scans and behavioral analysis tools are essential to identify and neutralize such threats.
Unauthorized Access
Preventing unauthorized access is crucial for maintaining security. Implementing Network Access Control (NAC) with 802.1X and RADIUS servers ensures only verified devices can connect. This reduces the risk of breaches and enhances overall system integrity.
Denial of Service Attacks
Denial of service (DoS) attacks disrupt operations by overwhelming systems with traffic. Volumetric attacks flood networks, while application-layer attacks target specific services. Mitigation strategies include traffic filtering and rate limiting.
Firewalls
Next-gen firewalls inspect encrypted traffic using SSL decryption, ensuring comprehensive protection. Stateful inspection and application-aware policies enable precise control over data flow. These features make firewalls indispensable for modern networks.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) monitor network activity for suspicious behavior. Signature-based tools like Snort detect known threats, while AI-driven solutions identify anomalies. Combining both approaches enhances detection accuracy.
Encryption
Encryption safeguards data during transmission and storage. AES-256, using XTS-AES mode, provides robust full-disk encryption. This ensures sensitive information remains secure, even if intercepted.
Virtual Private Networks (VPNs)
VPNs create secure tunnels for data transfer, protecting it from interception. WireGuard offers faster performance compared to IPsec, making it a popular choice. Both protocols ensure privacy and security for remote connections.
Regular Updates and Patches
Keeping systems updated is vital for addressing vulnerabilities. Zero-day response SLAs ensure timely patching, reducing the window of exposure. Automated patch management tools streamline this process, enhancing overall security.
| Security Measure | Key Feature | Benefit |
|---|---|---|
| Firewalls | SSL Decryption | Inspects encrypted traffic |
| IDS | AI-Driven Detection | Identifies anomalies |
| Encryption | AES-256 | Full-disk protection |
| VPNs | WireGuard | Faster performance |
Network Devices and Their Functions
Efficient communication relies on specialized devices that ensure seamless data flow. These tools play a critical role in maintaining connectivity, managing traffic, and optimizing performance across systems. From repeaters to gateways, each device has a unique function that contributes to the overall reliability of the network.
Repeaters
Repeaters amplify signals to extend the range of a network. They are commonly used in fiber optic systems, where transceivers like SFP+ and QSFP28 ensure high-speed data transfer. By boosting weak signals, repeaters prevent data loss and maintain consistent performance.
Bridges
Bridges connect multiple network segments, filtering traffic based on MAC addresses. Modern bridges use Spanning Tree Protocol (STP) to prevent switching loops, ensuring efficient data routing. Their filtering database operations enhance management by isolating unnecessary traffic.
Gateways
Gateways facilitate communication between different network protocols. They translate data formats, such as converting IPv4 to IPv6, enabling seamless interaction between diverse systems. This capability is essential for integrating legacy and modern infrastructures.
Brouters
Brouters combine the functions of bridges and routers, supporting both data link and network layers. They excel in legacy systems, routing protocols like IPX/SPX while bridging Ethernet traffic. This dual functionality makes them versatile tools for complex setups.
Network Interface Cards (NICs)
NICs connect devices to a network, enabling data exchange. SmartNICs, powered by FPGA-based packet processing, enhance performance by offloading tasks from the CPU. This innovation improves efficiency and reduces latency in high-demand environments.
- Repeaters: Extend signal range with fiber optic transceivers.
- Bridges: Use STP to prevent switching loops.
- Gateways: Translate protocols for seamless integration.
- Brouters: Support legacy IPX/SPX routing.
- SmartNICs: Enhance performance with FPGA processing.
Additional Network Components
Beyond the core elements, several supplementary tools enhance network performance and security. These devices and technologies ensure seamless connectivity, robust protection, and scalability for modern infrastructures.
Modems
Modems bridge the gap between local devices and internet service providers. DOCSIS 4.0 modems, for instance, deliver download speeds up to 10Gbps, making them ideal for high-demand environments. They support multi-gigabit PoE++ (802.3bt), providing up to 90W over Cat6A cables.
Network Cables
The choice of cables significantly impacts data transfer rates and reliability. OM5 fiber, for example, supports SWDM4 wavelengths, enabling efficient multi-channel communication. These systems ensure high-speed connectivity, even in complex setups.
Wireless Access Points (WAPs)
WAPs enable wireless connectivity, expanding network coverage. Wi-Fi 7 APs, with 320MHz channels and 4096-QAM, offer unparalleled speeds and efficiency. They are essential for environments requiring high-performance wireless access.
Intrusion Detection & Prevention Systems (IDPS)
IDPS monitor and protect systems from cyber threats. They operate in inline or passive deployment modes, ensuring real-time detection and mitigation. These tools are critical for maintaining network integrity and security.
Virtual Private Network (VPN) Appliances
VPN appliances create secure tunnels for data transfer, safeguarding sensitive information. IKEv2/IPsec protocols deliver throughput exceeding 20Gbps, ensuring fast and reliable access for remote users. These devices are indispensable for modern, secure infrastructures.
For a deeper dive into network devices, explore this comprehensive guide on network devices explained.
Conclusion
In today’s digital era, seamless connectivity and robust systems are essential for operational success. The interdependence between hardware and software ensures efficient data flow and reliable performance. Emerging trends like AIOps are revolutionizing network management, enabling proactive monitoring and automation.
Security remains a top priority, with zero-trust architectures becoming the standard. These frameworks verify every access request, minimizing vulnerabilities. Looking ahead, quantum networking promises unprecedented speeds and enhanced encryption, reshaping the future of connectivity.
To optimize your setup, focus on scalability and redundancy. Regularly update systems, adopt advanced protocols, and invest in AI-driven tools. By staying ahead of trends, you can build a resilient and future-ready infrastructure.
FAQ
What hardware is essential for building a computer network?
Key hardware includes Network Interface Cards (NICs), switches, routers, hubs, and cables. These devices ensure seamless data transfer and connectivity.
How do software components enhance network functionality?
Software like Network Operating Systems (NOS), protocols, and services manage communication, security, and resource sharing efficiently.
What are the common types of computer networks?
Popular types include Local Area Networks (LANs), Wide Area Networks (WANs), Metropolitan Area Networks (MANs), and Personal Area Networks (PANs).
What role do network topologies play in system design?
Topologies like bus, star, ring, mesh, and hybrid define how devices connect and communicate, impacting performance and scalability.
Why are network protocols crucial for data transfer?
Protocols such as TCP/IP, HTTP, FTP, SMTP, and DNS standardize communication, ensuring reliable and secure data exchange.
How can network security be strengthened?
Implementing firewalls, encryption, VPNs, and regular updates protects against threats like malware, unauthorized access, and denial of service attacks.
What are the functions of network devices like repeaters and gateways?
Repeaters extend signal range, bridges connect network segments, and gateways facilitate communication between different network systems.
What additional components support modern networks?
Modems, wireless access points, intrusion detection systems, and VPN appliances enhance connectivity, security, and performance.